UNLOCK YOUR NEXT
WAVE OF GROWTH
DISCOVER THE KEY STRATEGIES AND INNOVATIVE APPROACHES TO UNLOCK YOUR ORGANIZATION’S UNTAPPED POTENTIAL, PAVING THE WAY FOR UNPRECEDENTED GROWTH AND SUCCESS IN THE DIGITAL LANDSCAPE OF TODAY’S BUSINESS ENVIRONMENT.
CONNECTIVITY | VOICE | CLOUD | SECURITY
A DAY IN THE
CLOUD
JOURNEY INTO THE CLOUD WITH OUR EASY,
SCALABLE AND COST EFFECTIVE
ALL INCLUSIVE CLOUD SOLUTIONS
CONNECTIVITY | VOICE | CLOUD | SECURITY
HOST LOCAL
WORLD CLASS TECHNOLOGY
IN A HIGHLY SECURE, ALWAYS-ON FACILITY.
SUPPORT LOCAL
CONNECTIVITY | VOICE | CLOUD | SECURITY
THE NEXT WAVE
OF UNIFIED
COMMUNICATION
ALL INCLUSIVE VOICE SOLUTIONS FOR YOUR BUSINESS
CONNECTIVITY | VOICE | CLOUD | SECURITY
THE NEXT WAVE
OF BUSINESS
CONNECTIVITY
FAST, RELIABLE & SECURE FIBRE INTERNET
FOR YOUR BUSINESS
CONNECTIVITY | VOICE | CLOUD | SECURITY
UNLOCK YOUR
NEXT WAVE OF GROWTH
DISCOVER THE KEY STRATEGIES AND INNOVATIVE APPROACHES TO UNLOCK YOUR
ORGANIZATION’S UNTAPPED POTENTIAL, PAVING THE WAY FOR UNPRECEDENTED
GROWTH AND SUCCESS IN THE DIGITAL LANDSCAPE OF TODAY’S BUSINESS ENVIRONMENT.
CONNECTIVITY | VOICE | CLOUD | SECURITY
A DAY IN THE
CLOUD
JOURNEY INTO THE CLOUD WITH OUR EASY,
SCALABLE AND COST EFFECTIVE
ALL INCLUSIVE CLOUD SOLUTIONS
CONNECTIVITY | VOICE | CLOUD | SECURITY
HOST LOCAL
WORLD CLASS TECHNOLOGY
IN A HIGHLY SECURE, ALWAYS-ON DATACENTRE FACILITY.
SUPPORT LOCAL
CONNECTIVITY | VOICE | CLOUD | SECURITY
THE NEXT WAVE
OF UNIFIED
COMMUNICATION
ALL INCLUSIVE VOICE SOLUTIONS FOR YOUR BUSINESS
CONNECTIVITY | VOICE | CLOUD | SECURITY
THE NEXT WAVE
OF BUSINESS
CONNECTIVITY
FAST, RELIABLE & SECURE FIBRE INTERNET FOR YOUR BUSINESS
CONNECTIVITY | VOICE | CLOUD | SECURITY
Who We Are
Launched in 2010, CipherWave has established itself as a leading Tier 1 ISP, offering tailor-made, scalable, CONNECTIVITY, VOICE, CLOUD and SECURITY solutions.
We are a South African company with strong local roots & experience. Best described as the most connected ISP, we have extensive partnerships allowing us to provide best-in-class, global technology solutions and expertise, to growing South African businesses.
Our differentiator is the quality of our service backed by our customer engagement model. We own and manage our network infrastructure, which enables us to provide fast, reliable and efficient service and support to our customers.

Trust
We are reliable, and we act, speak and do as we say we will.
Respect
We value everyone and treat each other and our customers with dignity and professionalism.
Accountability
We own and manage our words, our actions and our results.
Integrity
We are responsible, honest and take the right actions every time because it is the right thing to do.
Loyalty
We are committed to represent the best interest of the brand and business in all our interactions internally and externally.




Trust
We are reliable, and we act, speak and do as we say we will.
Respect
We value everyone and treat each other and our customers with dignity and professionalism.
Accountability
We own and manage our words, our actions and our results.
Integrity
We are responsible, honest and take the right actions every time because it is the right thing to do.
Loyalty
We are committed to represent the best interest of the brand and business in all our interactions internally and externally.
CipherOnline
A comprehensive suite of connectivity solutions, including Layer 2 and 3 Fibre for fast and reliable national connectivity, Layer 2 and 3 Wireless for swift and cost-effective deployment, SD-WAN solutions like Fusion for enhanced speed and security, and global connectivity services that seamlessly link multiple branches over the internet.
CipherCloud
Embark on a transformative journey with CipherWave's Cloud Services, designed to revolutionize how you store, access, and manage data. Our comprehensive suite includes SaaS (Software as a Service), IaaS (Infrastructure as a Service) solutions, business continuity, and efficient email management.
CipherVoice
Unlock seamless communication with our all-in-one Voice Services, featuring Hosted PBX, VoIP, TMS, MS Teams Calling, Call Recording, Unified Communication, and SMS Bundles. Experience innovation with Talkk AI, our cutting-edge conversational system, offering 24/7 support and intelligent insights for informed decision-making.
CipherSecure
There is a rapid growing form of cybercrime and web security threats that makes firewalls one of the most vital components of any network.
Professional Services
CipherWave’s Professional Services is a dynamic and agile consulting partner with a strong foundation in global consulting expertise. We offer specialized consulting expertise in strategy, technology, and innovation.
Don't take our word for it
We are very fortunate to have formed excellent partnerships with all of our clients. This is what they have to say:




Shamith Maharaj, CEO
Shamith Maharaj, CEO of CipherWave, is a seasoned leader with a diverse background in Software Development and Network Engineering. With 15 years at CMC Networks, where he served as Vice President of Global Network Operations, and four years as an Executive at BCX overseeing Data Networks, Shamith's journey is marked by a commitment to excellence. A technology enthusiast, he transitioned to CipherWave in 2023 as Chief Business Development Officer before assuming the CEO position. Shamith's leadership style emphasizes adaptability, creativity, and key principles like Structure and Customer Centricity. He is recognized for leading successful teams and developing industry leaders.
— Wayne D’sa, CEO
Who We Work With
Like people, no two businesses are the same. That’s why we work closely with our customers to ensure that solutions are tailored to tick the boxes on their specific list of needs. Our bespoke solutions are able to support businesses across a wide range of industries:
Manufacturing
- ZimCo Group
- NGK Spark Plug
- Schmoltz & Bickenback
- Frankewen Forge
- SEW Eurodrive
Logistics
- Xeon Holdings (Pty) Ltd.
- Bombela Concession Company
Legal
- Scorpion Legal Services
Medical and Healthcare
- Diagnostic Radiological Service
- National Radiology Services
- Obsidian Health
- HealthRad
- MediHelp
Technology
- InfoProtect (Pty) Ltd.
- Disaster Recovery South Africa
- SwitchedOn IT
- Aerthyr IT
- Netsurit
- McGaric Technology Corporation (Pty) Ltd.
- Reef Business Systems
Media and Advertising
- Alliance Media South Africa
- Primedia Broadcasting
- Panalux
Retail
- Dischem
- Pandora
- Tiauto
It’s our unwavering focus on exceptional service and dedication to exceeding the expectations of our customers and partners that sets us apart.
— Wayne D’sa, CEO.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Turn constant change into your next wave of
business efficiency and unlimited growth.
CONNECTIVITY | VOICE | CLOUD | SECURITY
InsideCipherwave
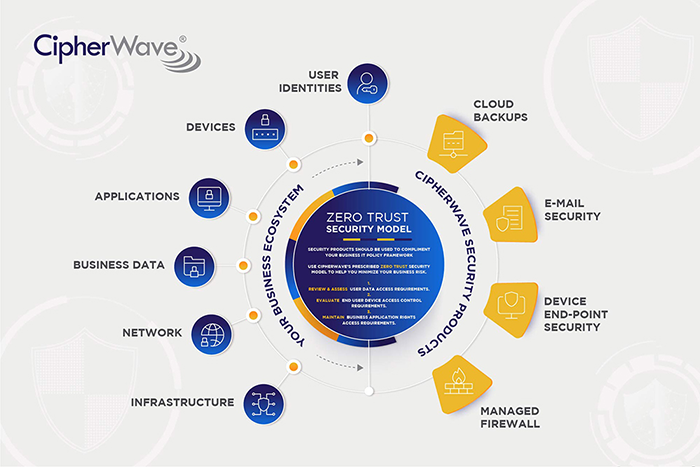
Mitigate security challenges via ‘Zero Trust’ strategy
In today’s highly-evolved security space, a conventional security approach is no longer good enough. Zero Trust should be viewed as the de facto security strategy.
Medium length display headline
Change the color to match your brand or vision, add your logo, choose the perfect layout, modify menu settings, add animations, add shape dividers, increase engagement with call to action and more. Change the color to match your brand or vision, add your logo, choose the perfect layout, modify menu settings, add animations, add shape dividers, increase engagement with call to action and more.
Feature three
Change the color to match your brand or vision, add your logo, choose the perfect layout, modify menu settings and more.




















